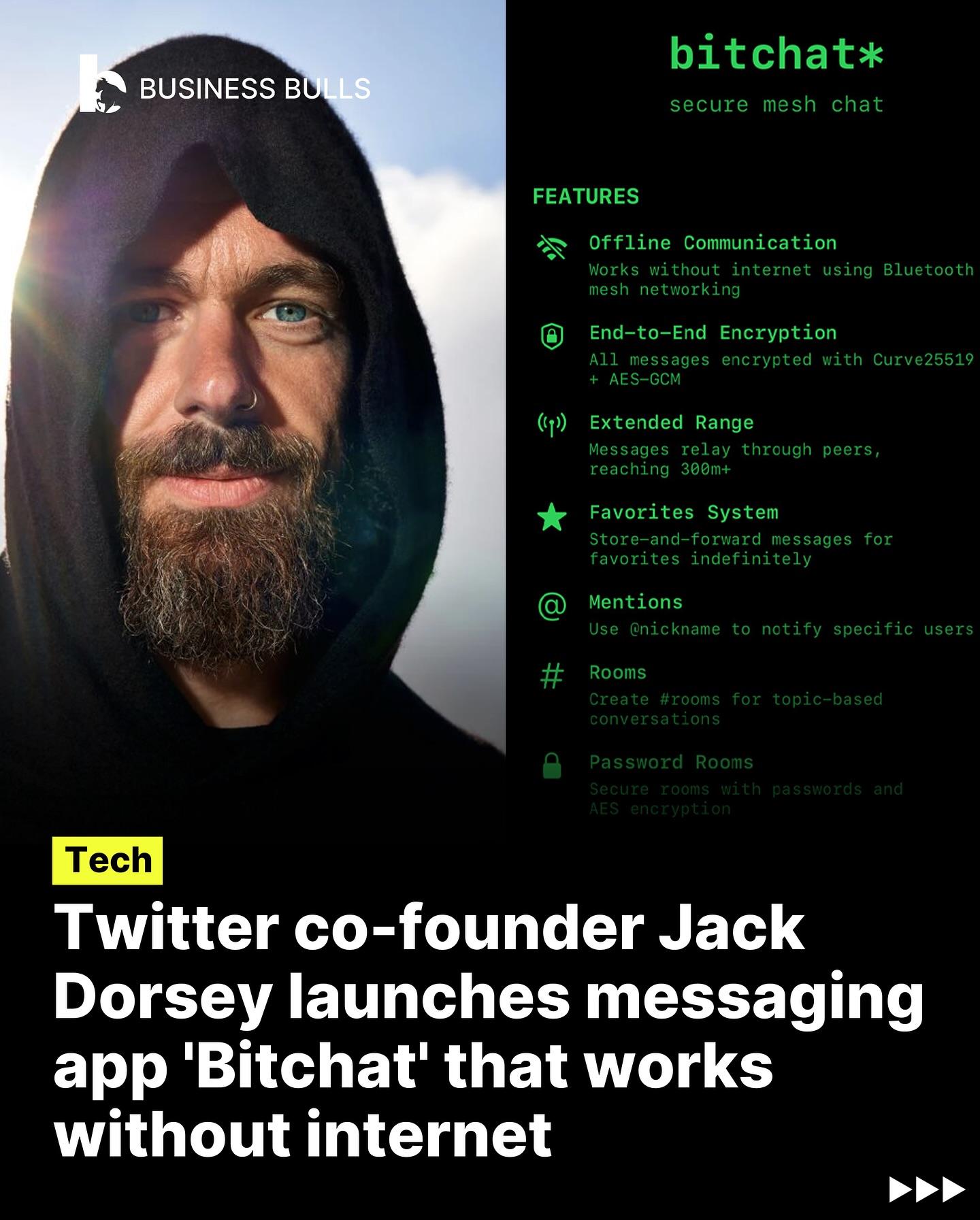
Humanity’s most powerful inventions could shape our future, or destroy it.
From nuclear weapons capable of erasing entire cities, to AI systems that might one day surpass their creators, and gene-editing tools that can heal or accidentally unleash new threats, technology has never carried more risk.
Autonomous drones can make decisions on their own, nanobots might replicate beyond control, deepfakes blur the boundary between real and fake, quantum computers threaten modern encryption, and cyberwarfare already disables nations without a single shot fired.
These breakthroughs reveal just how thin the line is between progress and danger. As we continue to create synthetic life and increasingly intelligent machines, our greatest challenge isn’t innovation, it’s maintaining control. Our future will be shaped by whether our wisdom can keep pace with our power.
Follow us @FutureTech for more!
From nuclear weapons capable of erasing entire cities, to AI systems that might one day surpass their creators, and gene-editing tools that can heal or accidentally unleash new threats, technology has never carried more risk.
Autonomous drones can make decisions on their own, nanobots might replicate beyond control, deepfakes blur the boundary between real and fake, quantum computers threaten modern encryption, and cyberwarfare already disables nations without a single shot fired.
These breakthroughs reveal just how thin the line is between progress and danger. As we continue to create synthetic life and increasingly intelligent machines, our greatest challenge isn’t innovation, it’s maintaining control. Our future will be shaped by whether our wisdom can keep pace with our power.
Follow us @FutureTech for more!
Humanity’s most powerful inventions could shape our future, or destroy it.
From nuclear weapons capable of erasing entire cities, to AI systems that might one day surpass their creators, and gene-editing tools that can heal or accidentally unleash new threats, technology has never carried more risk.
Autonomous drones can make decisions on their own, nanobots might replicate beyond control, deepfakes blur the boundary between real and fake, quantum computers threaten modern encryption, and cyberwarfare already disables nations without a single shot fired.
These breakthroughs reveal just how thin the line is between progress and danger. As we continue to create synthetic life and increasingly intelligent machines, our greatest challenge isn’t innovation, it’s maintaining control. Our future will be shaped by whether our wisdom can keep pace with our power.
👉 Follow us @FutureTech for more! 🔌
·238 Views
·0 Vista previa